
IRM protection and control platform for Enterprise
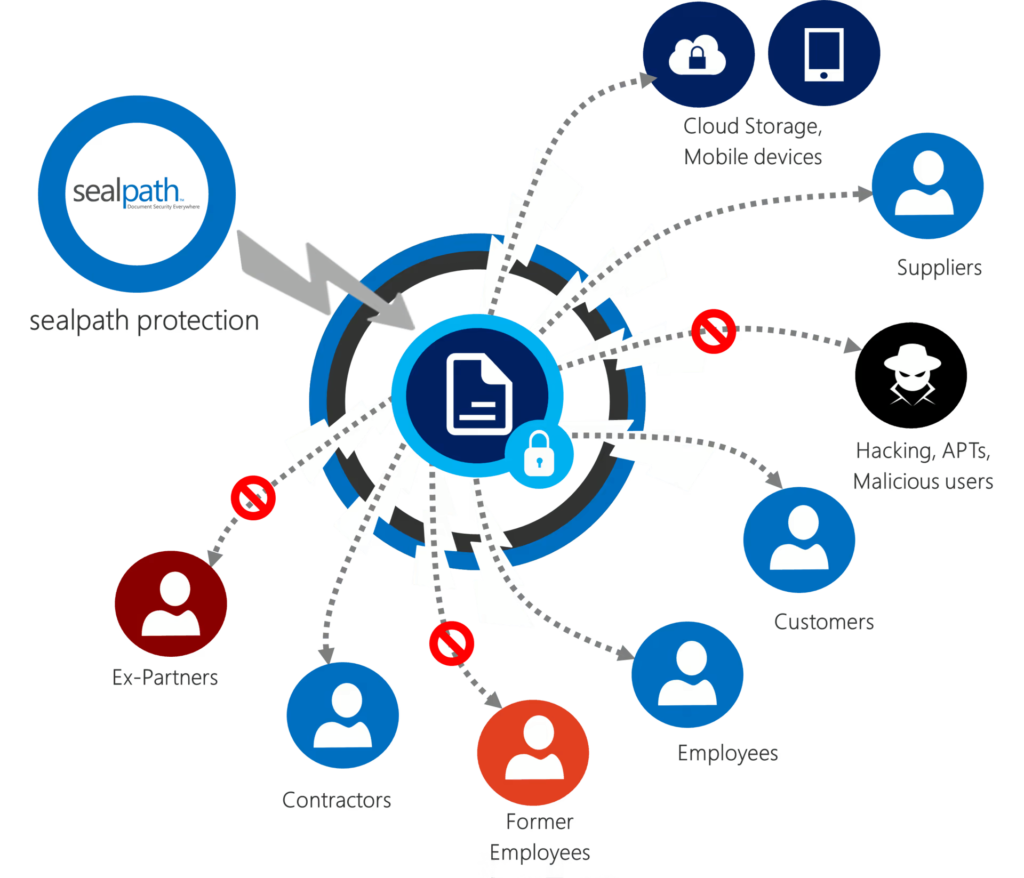
SealPath Protects and Controls Corporate Data. Wherever they travel
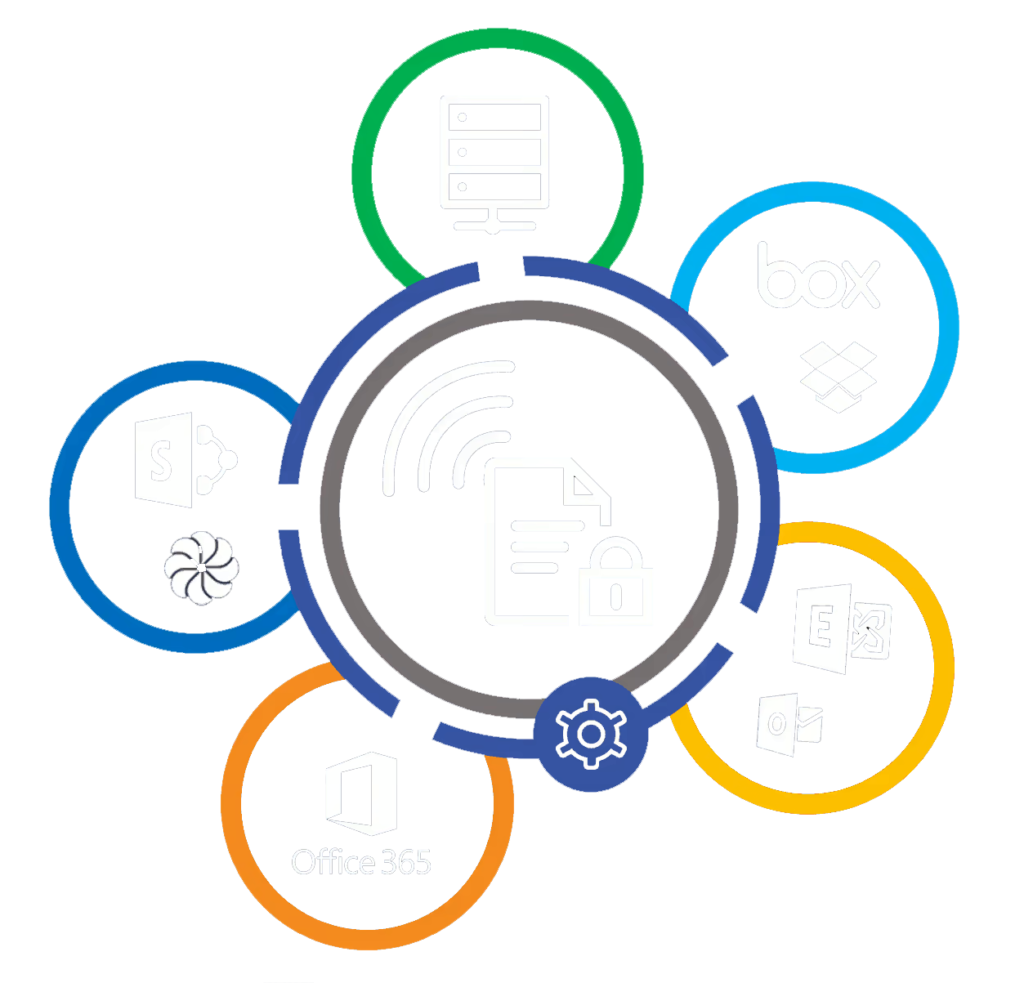
SealPath protection accompanies the document both on your network and on customers’ or partners’ networks, in the cloud (e.g. Box, Dropbox, etc.) or on a mobile device. It controls who accesses the data, when and with what permission (read only, edit, print, copy and paste, etc.). You can see the details of accesses to the document and if anybody has attempted to gain access without permission. If you cease to collaborate with the holder you can block or delete the document so that it is inaccessible to that user or anyone else.
Ease of use
SealPath is designed to provide the greatest ease of use and flexibility for both end users and IT personnel
Automation
Documents only need to be put in the network folder or document manager library to be protected by the automatic folder protection function
Cloud + On-Premise
Deploy it in cloud mode to avoid installing server or on-premise components for total control of the infrastructure
Integration
SealPath integrates with your Active Directory or SIEM LDAP tools, DLPs and corporate document managers.

Granular permission control
- You can include granular authorisation for access to the information.
- Set expiry dates, watermarks, off-line access, etc.
- Delete documents remotely even if they have already been sent.
- Users can create their own policies and controls.
- Policy management by department. Automate protection.
Use your usual tools
- Native integration with Office without requiring installed agents.
- Open protected PDFs with Adobe, Foxit, Nitro, Nuance, etc.
- Native integration with AutoCAD, SolidEdge, etc. No viewers required.
- Supported on Windows, Mac OSX, iOS and Android.
- Use Microsoft Outlook to send protected emails.
Extremely simple sharing
- Automatic sending of invitations to external users.
- Super-convenient self-registration in seconds.
- Option of customising invitations and the registration portal.
- Automatic registration and single-sign-on for internal users.
- Additional centralized controls for the administrator

Exhaustive access control
- Audits accesses and the use of protected documentation.
- Available to the user it protects and to administrators.
- Alerts for attempts to access by blocked users, breached docs, etc.
- Risk control reports on the documentation.
- Powerful Top10 graphics, filterable lists, exportables, etc
Automation of the protection
- Automatic protection for file servers, NAS devices, etc.
- Automatic protection of SharePoint libraries.
- Automatic protection of folders in Office 365.
- Automatic protection in Box, Dropbox and Cloud storage.
- Automatic protection in the email through Outlook and Exchange
Integration with corporate systems
- Seamless integration with Active Directory and LDAP.
- Option of working with groups and domain credentials.
- Integration with SIEM tools.
- Integration with DLP solutions (e.g. Symantec DLP).
- Specific integration with simple, flexible SDK




