
Secure your devices with the #1 malware removal and protection software
Why Malwarebytes endpoint security?
Quickly recover to a pre-attack state
72-hour ransomware rollback plus removal of related artifacts and configuration changes (EDR version).
Easy to deploy and use
Our cloud-platform stands up within hours and is easy-to-use, even for emerging users.
Stops threats at the perimeter
Inherent protection against brute force attacks, zero-day threats, and common infections
Efficient cybersecurity operations
Malwarebytes' platform makes it easy to reinforce prevention with cloud-launched expansion modules
MRG EFFITAS 360° ASSESSMENT & CERTIFICATION: BADGES ACROSS THE BOARD





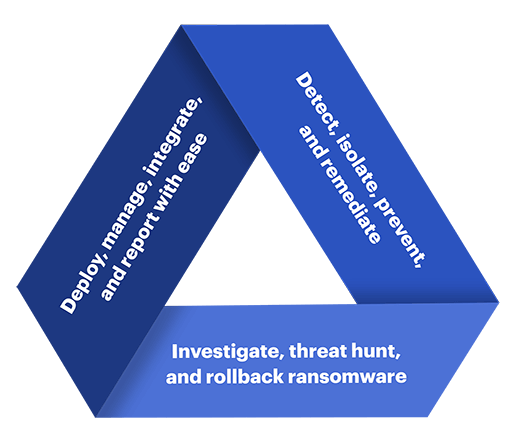
Three critical EDR features
Detection and protection against ransomware, malware, trojans, rootkits, backdoors, viruses, brute force attacks, and “zero-day” unknown threats that other EDR tools don’t catch.
Efficient
We believe cybersecurity technology should be available for every business, no matter how big or small. Our products are safe and secure, powerful, Cloud native, affordable and easy to use – without needing specialist skills or qualifications
Effective
Stop wasting time on manual searching and follow up – we do the heavy lifting! Automated searches for your data and threats to your business run around the clock. Automated alerts provide actionable insights as soon as information is detected
Easy
Malwarebytes Endpoint Detection and Response for Windows and Mac can easily replace or augment other endpoint security solutions, including Microsoft Defender.
- Non-disruptive, role-based access, deploy within minutes
- Lightweight endpoint agent, robust integrations
- Intuitive cloud-native management console
Malwarebytes next-gen EDR tool
Low false positive alerts
The average enterprise security team spends over 25 percent of their time chasing thousands of false positive alerts each month (Ponemon).
Improved threat detection
Sophisticated attacks exploit entry points and security vulnerabilities, and once attackers are inside, they can set hooks that cause serious damag
Remote worker protection
Higher Remote Desktop Protocol (RDP) usage resulting from the COVID-19 pandemic have exposed an exploitable vector for ransomware.
Innovative active threat response
keeps endpoints productive
Ransomware rollback
For Windows environments, paying ransomware is no longer a requirement.
Automated remediation
Find and reverse all major and subtle changes made by malware.
Attack isolation
If an endpoint is attacked, you can easily halt malware from spreading and causing harm.
YOUR COMPLIMENTARY THREAT ASSESSMENT - ASK OUR TEAM
Don’t underestimate the infection rates of your endpoints. Our complimentary Threat Assessment will help you identify areas of risk that your current provider might not be able to identify.
Ask our team about receiving an assessment built for you.




