
The Most Advanced
Encryption Software
Unique solution that ensure the highest level of
communication confidentiality and anonymity.
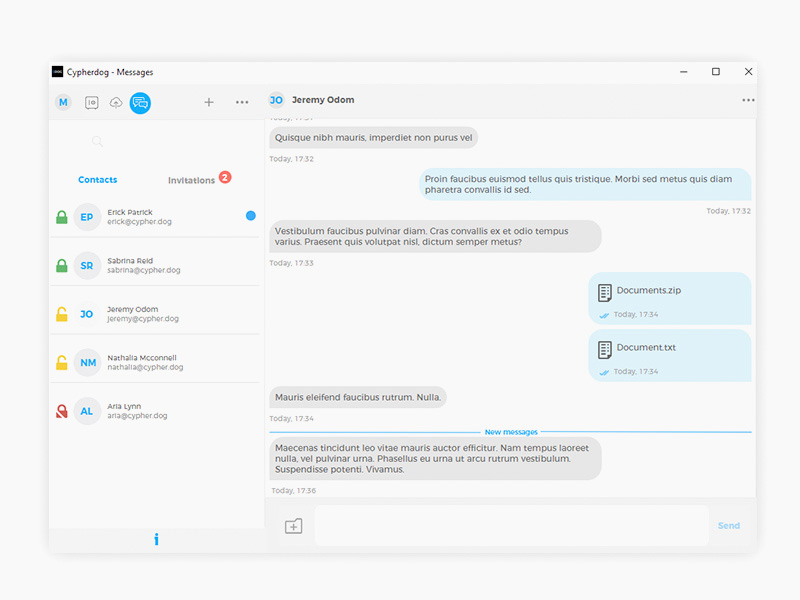
Send files securely
Send files in all formats and sizes in a secure way with end-to-end encryption allowing you to share files among your contacts, ensuring that nobody is able to intercept them.
Neither we nor any other “trusted third party” has access to your files. At the same time, thanks to confirming the identity of your contacts, you know for sure that no one will be able to impersonate the person you are communicating with.

No "trusted third party"
Cypherdog does not use e-mails and SMS to confirm the identity of its communication users. It does not use any third party global organizations, such as Google, Facebook, Apple or Microsoft, and other providers, e.g. electronic signatures or certification centers.

Public keys in blockchain
Public keys used to encrypt transmitted files and communication content are stored in distributed registers using blockchain technology. This guarantees protection against data loss and leakage.
Local encryption
By using Cypherdog you have the option to encrypt files that you manage on your local device using the application. You can also save them to your device in an encrypted format.

Exclusive access to the private key
As a user, you are the only person who has access to the private key that you create when logging in to the application for the first time. It is not possible to recover the private key, this means that no one but you can access it.

Ranking of credibility in blockchain
If you want to send a file to someone and need to check if this is the person they claim to be, all you have to do is check their credibility ranking, that is, the number of other people's identity confirmations.

End to end encryption
The data you send or receive is encrypted from the moment it is sent until it is received by the recipient. You cannot decrypt files without a private key which is only found in the Cypherdog application.
Encrypted cloud
Through the application you have access to a private encrypted cloud in which you can place your files in a completely secure way. It is your private space for keeping important documents, files, contracts and invoices.

No administrator access to data
As a data administrator, Cypherdog does not have access to the user's address book or their contact network. During the process of transferring files between parties, the administrator does not have access to files in any form.

Zero-knowledge security
The service provider cannot help you to recover encrypted data or gain access to your account in case you lose your login details. Zero-knowledge security guarantees real data confidentiality and privacy.
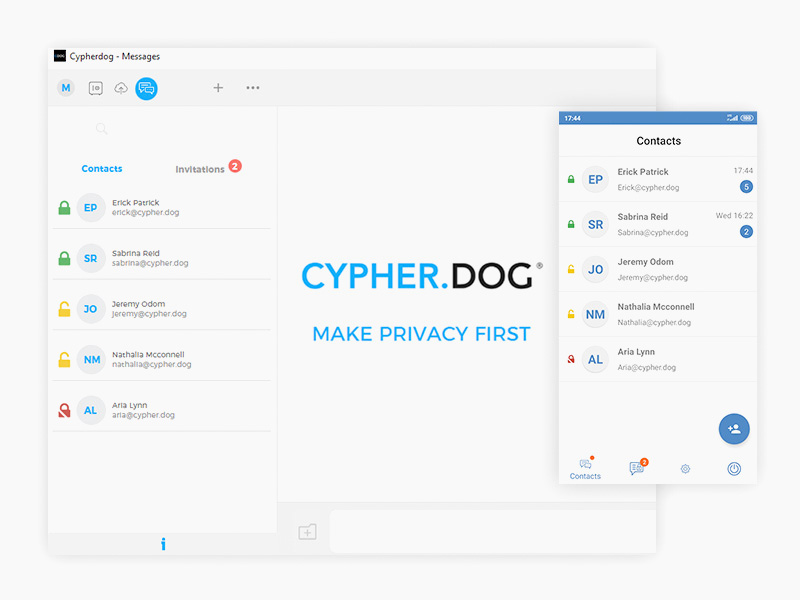
Use chat with encrypted communication
- all address books of our users are encrypted (featuring full anonymity of contacts),
- we don’t know who our users invite to chat (fully anonymous conversation),
- we don’t know when or who is talking to whom (full anonymity of communication),
- we don’t know what users are sending with end-to-end encryption (full confidentiality and message integrity),
- we do not save any data on our servers’ hard drives (all communication is carried using RAM),
- all encrypted anonymous messages on our servers are completely removed after 24 hours and no trace is left of them (no data is saved to
Manage your files in an encrypted cloud
Secure place to store documents, contracts and reports that no one else can have access to? You can store files in your secure cloud, which only you can access from our application. Use our encrypted cloud as a secure archive of your most important data.
We don’t use web client applications. Access to services is available in a desktop application.
Encrypt files locally on your device
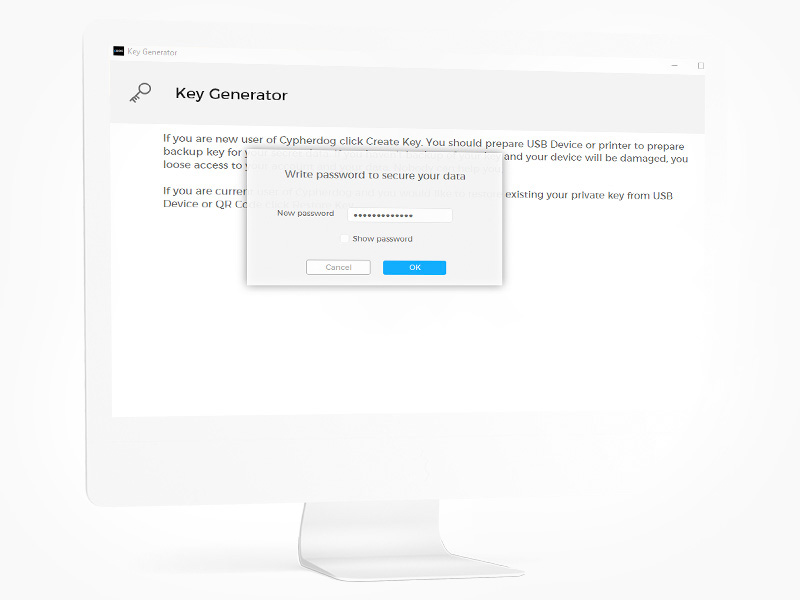
The private key that protects all communications in the system is ONLY on your disk.
Only YOU have access to a key that allows you to encrypt your files, conduct chat conversations, manage your devices and address books. Encryption of all communications is always done locally on your device.
This can be used to locally encrypt your confidential files.




