Perimeter81 Webinar
https://youtu.be/UCJs34jVolMSometimes it isn’t enough to “set and forget” – you need an in-depth view of your networks and policies. The monitoring dashboard from Perimeter81, gives you a minute-to-minute view of…
https://youtu.be/UCJs34jVolMSometimes it isn’t enough to “set and forget” – you need an in-depth view of your networks and policies. The monitoring dashboard from Perimeter81, gives you a minute-to-minute view of…
Gartner® Report How to Select the Right ZTNA Offering Choosing a ZTNA solution that’s right for your organization’s network security Download The Report Get Gartner® insights into choosing the right…
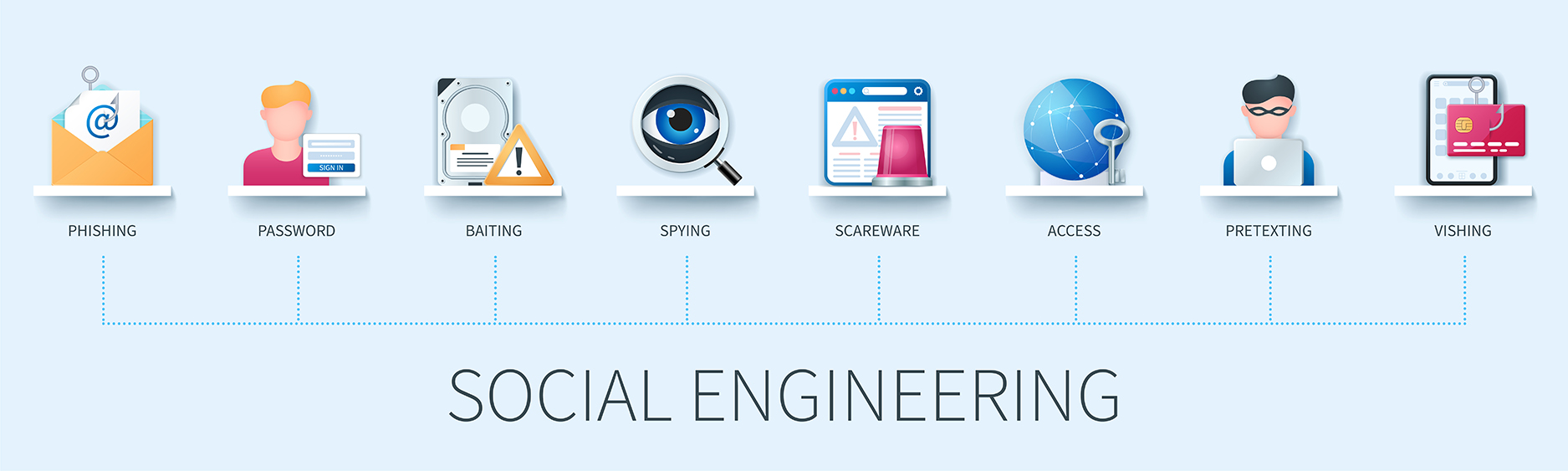
What are Social Engineering Attacks?Social Engineering is an act of manipulating people to expose confidential or sensitive information.This can be done by telephone, email, or face-to-face contact. It is the…
20 CRITICAL SECURITY CONTROLS Developed and periodically updated by a global community of experts, the 20 controls are “the most effective and specific set of technical measures available to detect,…
Use these 20 CRITICAL SECURITY CONTROLS Developed and periodically updated by a global community of experts, the 20 controls are “the most effective and specific set of technical measures available…